Oracle MAF store bypass

This blogpost is a direct copy of previous research i have done at PenTestPartners. The original post resides here: https://www.pentestpartners.com/security-blog/oracle-maf-store-bypass-a-how-to/
This blog post is purely for archive purposes only
On a recent assignment I was asked to look at the security of a cloud-based solution for expenses, the Oracle® ExpensesCloud with Fusion applications. It was being used for employees to create/save/edit/submit claims to the employer.
TL;DR
Having default hardcoded credentials allows an attacker effortless compromise of the credentialed action. In this instance the attack allows someone to inject a custom Certificate Authority into the application’s KeyStore allowing the attacker to man-in-the-middle the traffic for further analysis!
Let’s get into it
Each employee had a work mobile phone with the “Oracle: Fusion Mobile Expenses” application installed, so the first step was to replicate it in my Android phone testing environment.
Not the actual environment ?
Cert pinning bypass?
The application uses its own SSL/TLS KeyStore, outside of the normal device cert repository, so normal Cert pinning bypass techniques won’t work. Trust me I tried a lot!
Onwards to the KeyStore
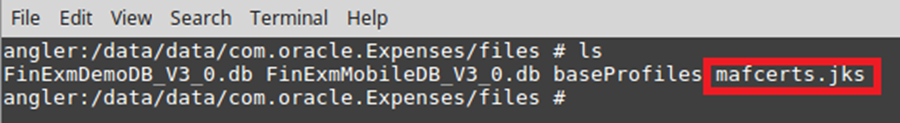
Once the application was installed I found an interestingly named file called “mafcerts.jks” in the application data folder. On android it’s located here “/data/data/com.oracle.expenses/files/mafcerts.jks”
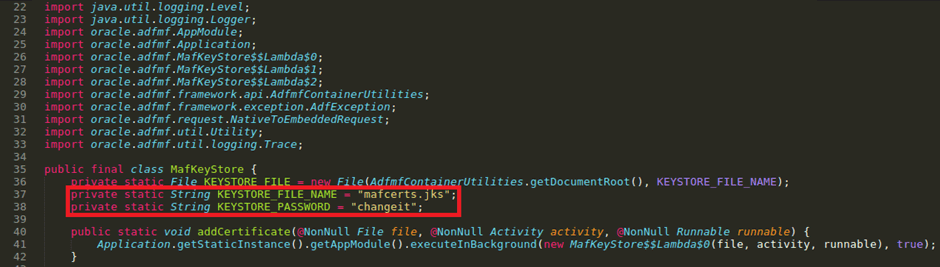
As always I decompiled the application to look through the source code looking for interesting strings. Specifically I wanted to know if there was any info on the “mafcerts.jks” in the source code.
There was:
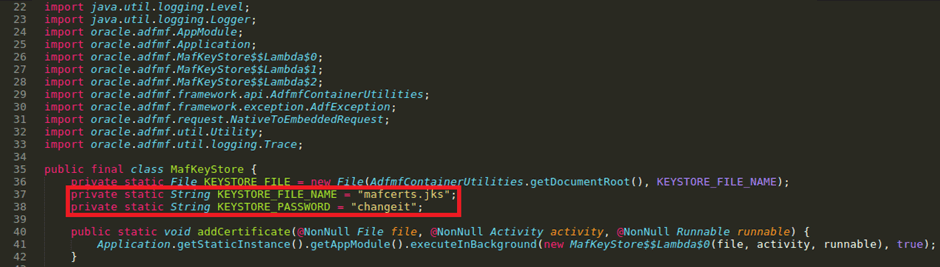
Great, we now have the hardcoded creds for the keystore. ?
NOTE: these default creds are very well known in the Java/Oracle world for all KeyStores
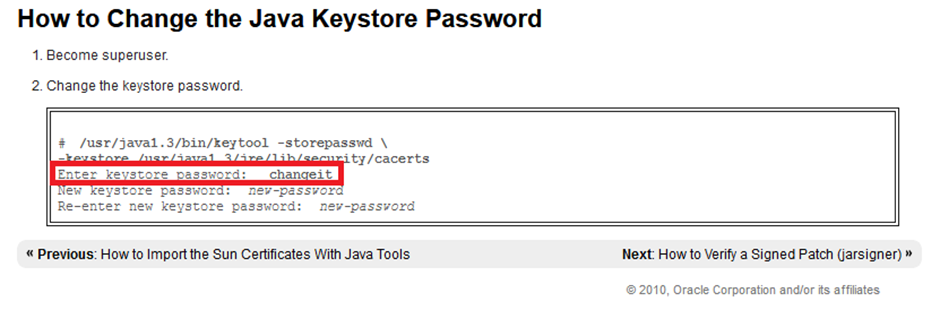
Source: https://docs.oracle.com/cd/E19957-01/817-3331/6miuccqo3/index.html
Time to Burp
So, the next step was to try and add my own “Burp CA” into the file to be able to MiTM the apps https traffic.
Download the “mafcerts.jks” file to your computer.
You will also need the Burp CA file too, here is how to do that: https://support.portswigger.net/customer/portal/articles/1783075-Installing_Installing%20CA%20Certificate.html
Rename the Burp certificate filetype to end in *.pem instead of *.cer
If you have java installed on your Linux distro you should be able to run “keytool” from anywhere, but if not try these steps:
“find / -name jre” “cd /path/to/jre/location” “./keytool”
Once you can run “keytool” and have both “mafcerts.jks” and “<burpcafile>.pem” you can now add Burps CA file to the KeyStore.
“keytool -import -trustcacerts -alias portswiggerca -file burpcert.pem -keystore mafstore.jks”
It will then ask you for the password “changeit” as found earlier.
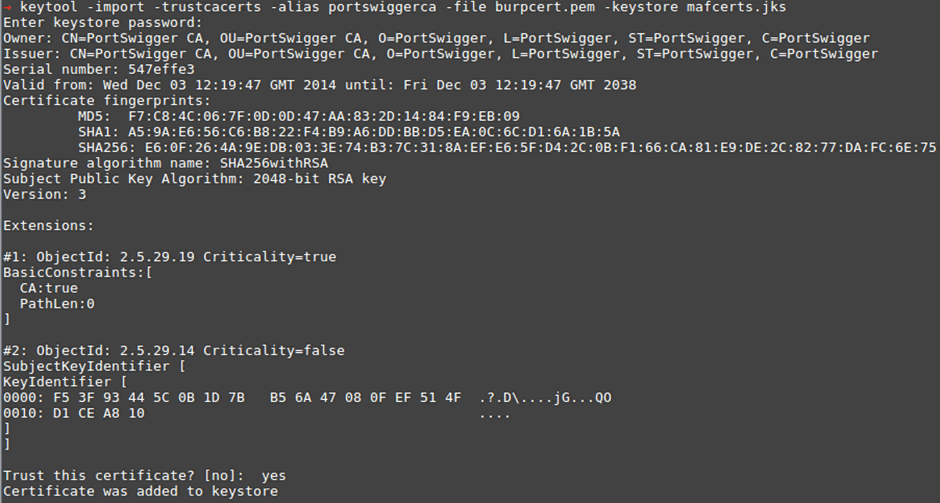
It will ask you to “trust” this new cert. Type “yes” and you’re done. Now you can verify the new cert has been added to the KeyStore:
“keytool -list -v -keystore mafcerts.jks | grep Alias”
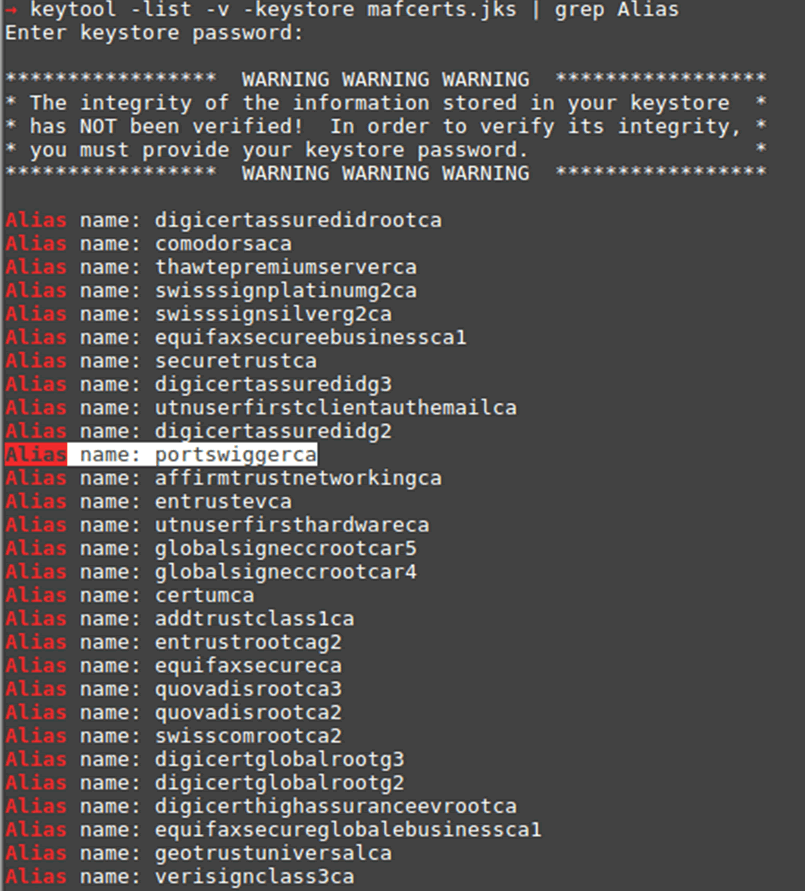
Now all you have to do is replace the “mafcerts.jks” file in the application directory on the phone (using ADB for android) and restart the app.
MiTM time
Additionally, you can now MiTM the application in the normal way with proxy droid or via the wireless proxy settings.
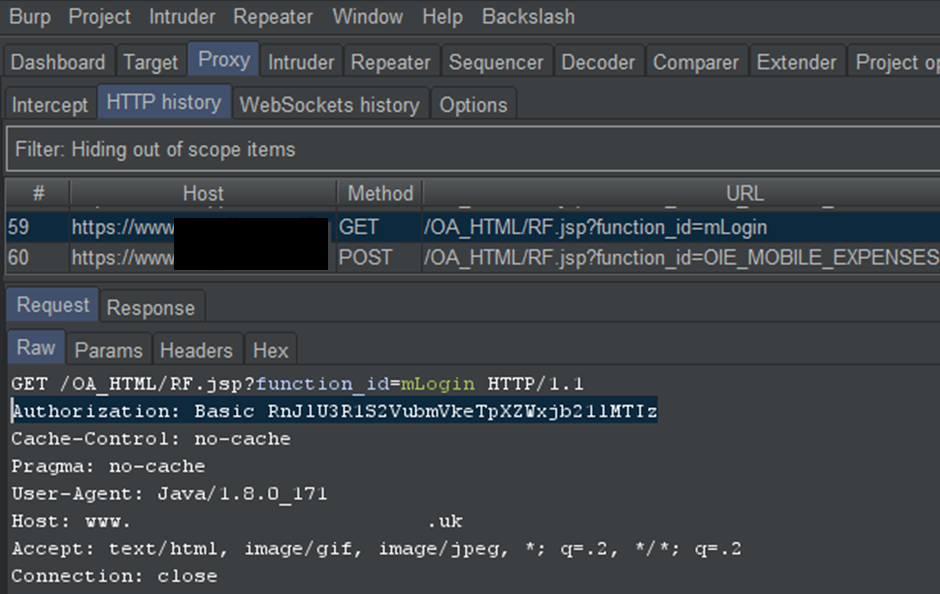
PS. if you see Oracle built apps, they mostly use this method of cert pinning. Don’t waste a day like I did!
