TPM Sniffing Greatness!
A few months back i was doing a "Stolen Laptop Assessment"
The assessment was conducted locally via a pre-built laptop. The laptop was built with BitLocker Drive encryption that was tied into the Trusted Platform Module (TPM2.0). The focus of this testing was to determine whether the BitLocker key could be retrieved from a hardware attack.
Upon opening the laptop case, it was noticed that there was a physical switch, these sometimes are configured to stop the laptop booting after any access has been gained to the internal laptop hardware. These switches are also known as ‘Tamper Switches’.
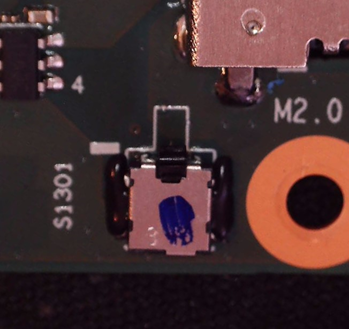
Subsequently this was ‘Hot Glued’ down to hopefully prevent any safety feature being triggered.
Further investigation of the laptop hardware showed that a Discrete TPM[1] module (ST33TPHF2XSPI[2]) was present and utilised the SPI protocol[3] to communicate with other parts of the hardware such as the UEFI bootloader and main processor (CPU). SPI communication lines were traced out to debug test points on the motherboard.
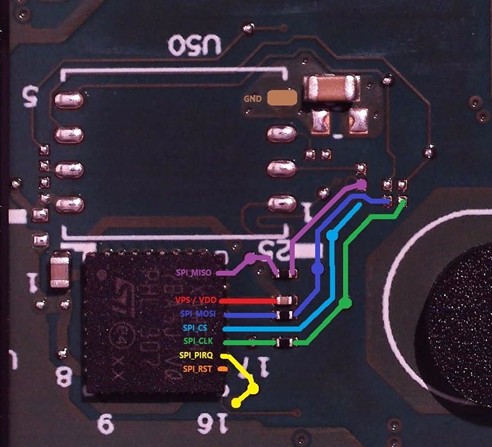
Small wires were then soldered to the relevant pins (MISO, MOSI, CLK and CS) to be able to read the SPI communications. These wires were also ‘Hot Glued’ to stop any detachment while the laptop was being put back together.
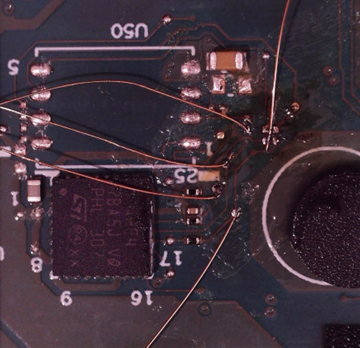
The laptop was reassembled to a working state where normal functionality was resumed, and Windows would boot up to the login screen.
Using a logic analyser (Salea Logic Pro 16) the SPI communication was sniffed to see if any BitLocker Volume Master Key (VMK) could be retrieved.
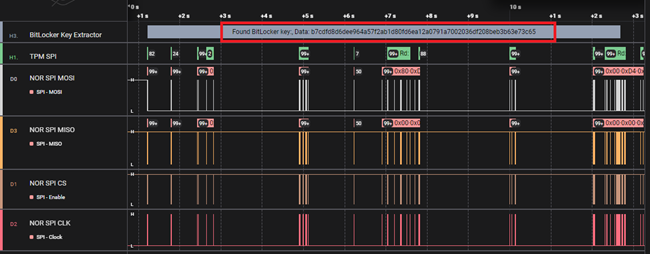
With the BitLocker VMK in hand, it was possible to decrypt the SSD thanks to dislocker[4] and extract the SAM/SYSTEM files for further exploitation and privilege escalation.
$ hexdump -C vmk
00000000 b7 cd fd 8d 6d ee 96 4a 57 f2 ab 1d 80 fd 6e a1
00000010 2a 07 91 a7 00 20 36 df 20 8b eb 3b 63 e7 3c 65
$ sudo dislocker -v -V /dev/sdb3 --vmk vmk – /media/bl
$ sudo mount -o ro,loop /media/bl/dislocker-file /media/blm
$ ls /media/blm
'$RECYCLE.BIN' OCD 'Program Files (x86)' Users Windows ProgramData swapfile.sys pagefile.sys hiberfil.ysy 'Documents and Settings' 'Program Files' Scripts 'System Volume Information' DumpStack '.rnd'
$ ls /media/blm/Users
'All Users' Default 'Default User' ensadmin Public stuart 'desktop.ini'
Anyways, after i did all that, i had about 30 different tabs open on my browser just for TPM info and previous examples, This caused me pain!
So i set up a centralised repo of all TPM Sniffing blogs and resources!
[1] Discrete TPM, or dTPM, is a separate component that is physically connected onto the motherboard to provide hardware-based encryption.
[2] https://www.st.com/en/secure-mcus/st33tphf2xspi.html
[3] https://en.wikipedia.org/wiki/Serial_Peripheral_Interface
